撸个简单的权限系统:用户包含角色, 角色包含权限
先定义一份简单的权限规则库
相当于定义菜单权限
casbin.conf
1 | [request_definition] |
- request_definition: 可以理解为验证函数传进去的参数
- policy_definition: 可以理解为添加规则函数传进去的参数,就是存进数据库的数据规则
- policy_effect: 对结果进行判定
- matchers: 匹配规则
先测试一下:
1 | func main() { |
增加组的权限
相当于角色权限 和 用户权限
casbin.conf
1 | [request_definition] |
- role_definition: 分组功能
测试代码
1 | package main |
很简单,wisp拥有yy角色,yy角色包含test.a1 /test/a1 get 权限
怎么结合到iris里面去呢,想来想去也想不懂,总不能把用户系统写到casbin里面来吧,要不就添加用户权限的时候更新一下casbin数据库,要不就登陆或者刷新的时候把用户权限写进casbin数据库,感觉麻,还是后面这种方便一点
先增加一份初始化代码
datasource/casbin.go
1 | package datasource |
增加casbin规则的增加、删除方法
repo/login_repo.go
1 | package repo |
主要就是利用casbin的两个API:
- enforcer.RemoveFilteredPolicy
- enforcer.AddPolicy
用户刷新的时候更新一次casbin权限
说白了当这个东西是个缓存来用
services/login_service.go
1 | func (l *loginService) Info(tokenString string) (response datamodels.Response) { |
用户登陆或者刷新后数据库保存的规则如下:
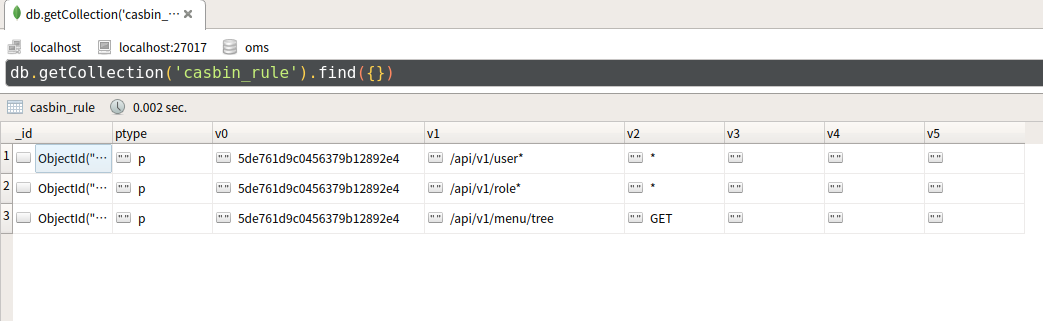
增加中间件验证权限:
middleware/casbin_middleware.go
1 | package middleware |
把中间件添加进路由
route/route.go
1 | package route |
大功告成~